Vulnerability Response Process

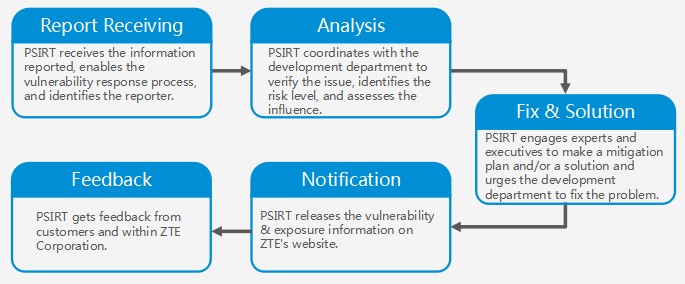
The time for completing a vulnerability response process depends on the scope of the vulnerability.
If you report a vulnerability to ZTE, we assume that you agree to keep the information confidential before ZTE discloses the information. Likewise, ZTE is committed to keeping the sensitive information secret for customers before repairing and disclosing the vulnerability.
ZTE uses the CVSSv3 to score and rate each vulnerability. Reporters can also score/rate vulnerabilities for our reference.
ZTE uses CVE (Common vulnerabilities and Exposures) and CWE (Common Weakness Enumeration) to quote public vulnerabilities outside ZTE’s official website.
ZTE reserves the rights for releasing vulnerability reports.