ZTE PSIRT
ZTE Product Security Incident Response Team (PSIRT) receives, handles, and discloses security vulnerabilities related to ZTE's products and solutions, and is the channel to disclose vulnerability information. The PSIRT is also responsible for formulating ZTE's security incident management policy and security incident solution, analyzing vulnerabilities and patches released by system software providers and security organizations, and responding and handling security incidents released by customers, security organizations, or individuals.
ZTE encourages cybersecurity researchers and industry organizations to report security vulnerabilities related to ZTE products. ZTE PSIRT will follow industry standards such as ISO/IEC 30111 and ISO/IEC 29147 to handle received security vulnerabilities.
ZTE PSIRT Email: psirt@zte.com.cn。
Security Vulnerability Submission
Vulnerability Response Process
Security Bulletins
ZTE Bug Bounty Program
ZTE encourages global security practitioners and industry organizations to proactively submit security vulnerabilities of ZTE products, helping us continuously improve security of our products and services. If you have discovered any security vulnerabilities, please submit them to us in a timely manner.Submitting channel: psirt@zte.com.cn.
Submitting scope: Products within the scope of ZTE service (excluding End of Service & Support products). If the relevant product is within the scope of the ZTE bug-bounty program, the corresponding reward will be provided.
Vulnerabilities will be addressed as soon as we receive them. Generally, you will get
an email of confirmation within 1 working day from submission;
an email of verification within 7 working days;
Subsequently, we will keep you updated with the latest progress during the vulnerability handling process.
To ensure handling efficiency, please follow the following guidelines to provide a vulnerability report:
1.Fill in the template completely and accurately.
2.As security vulnerabilities are sensitive information, we strongly suggest you use our PGP public key (key ID: FF095577) to encrypt the information you submit.
3.Use the Email subject format as: [Product Name-Vulnerability Overview]
4.Ensure that your submission does not involve intellectual property issues, and does not contain the contents prohibited by law or profanities.
In addition, we assume that you agree to keep the information confidential before ZTE discloses the information. At the same time, ZTE is committed to keeping the sensitive information confidential for customers before remediation and disclosing the security bulletin.
For non-security vulnerabilities, please consult Global Technical Support。
"Security in DNA, trust through transparency" is ZTE’s vision on cybersecurity, ZTE is committed to delivering secure and trustworthy products and services to customers. ZTE performs security governance that covers the supply chain, R&D, delivery, incident response, and various support fields, forming a cybersecurity assurance system throughout the product lifecycle. Abiding by laws and regulations, following industry standards and customer needs, ZTE PSIRT formulate the ZTE vulnerability response process.
ZTE attaches great importance to vulnerability management throughout the product lifecycle, and formulates a complete vulnerability response process in accordance with ISO/IEC 30111 and ISO/IEC 29147 standards to ensure that security vulnerabilities are effectively and rapidly handled to reduce security risks.
The security vulnerability response process includes five steps:
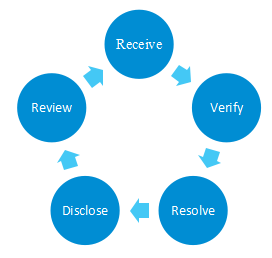
1.Receive: Receive vulnerabilities discovered from the various relevant parties.
ZTE encourages global security practitioners and industry organizations to submit security vulnerabilities of ZTE products. Meanwhile, ZTE PSIRT proactively search for threat intelligence released by the industry and identifies effective vulnerability information.
2.Verify: Verify vulnerabilities, analyze impacts, and assess risks.
ZTE PSIRT analyzes and verifies security vulnerabilities, and grades and scores vulnerabilities in accordance with the CVSS standard. Relevant security experts further review and confirm the verification result. The security vulnerabilities within the scope of the ZTE’s bug-bounty program will be rewarded.
3.Resolve: Provide mitigation measures and solutions, after confirming that a product is affected by the vulnerability.
For confirmed security vulnerabilities, PSIRT collaborates with the product team to formulate, develop, and provide vulnerability remediation solution (including mitigation measures and solutions), effectively addressing security risks, and ensuring the security and stability of customer data and systems.
4.Disclose: Maintain communication, fix vulnerabilities and disclose vulnerabilities.
During the process of vulnerability response, ZTE keeps communication with the customer and related parties, synchronizes the handling progress, assists the customer in remediating vulnerabilities as soon as possible, and completes coordinated disclosure of vulnerabilities.
5.Review: Accumulate experience from perspectives of management, technology, etc. to improve the efficiency and capability of vulnerability management.
ZTE will conduct managerial and technical root cause analysis, summarize lessons learned, continuously optimize vulnerability response processes, and improve product security to deliver secure and trustworthy products and services to customers.
Vulnerability Disclosure Policy
ZTE discloses vulnerability information and remediation solution in the following ways:
Security Bulletin: A security bulletin includes the vulnerability severity level, scope of affected products and versions, business impact, and remediation solution. It is usually used to disclose the information and remediation solution of serious and high-risk security vulnerabilities of ZTE products, so that customers can obtain the vulnerability information and evaluate risks. ZTE reserves the right to release and continuously update vulnerability bulletins.
Security Statement: A security statement includes a description of vulnerabilities that have a wide impact on the industry or society, a brief description of relevant security topics, and ZTE’s latest handling progress. It is used to disclose important security topics (including security vulnerabilities and non-security vulnerability topics), so that relevant parties can stay informed of the progress of ZTE's handling progress.
Release Notes: A release note includes information about remediated vulnerability of ZTE products. It is used to disclose security vulnerabilities that have been remediated during the R&D process, so that the customers can understand the product’s security status.
Additional Information
1.ZTE PSIRT will strictly control the scope of vulnerability information, ensuring it is only shared among those directly involved in the vulnerability remediation process.
2. ZTE PSIRT has the right of interpretation for the above policy.

Insisting on the principle of being open and transparent, ZTE ensures that it exposes potential product vulnerabilities, including final solutions, to customers in a timely manner.
As a member of the FIRST and a CVE Numbering Authority (CNA), ZTE is dedicated to publishing vulnerability exposures jointly with customers and stakeholders in a more open manner. Relevant exposures can be found on CVE and ZTE website.
Click Bulletin -Security Bulletins for more information.

ZTE is committed to continuously improving security of its products and services to provide users with secure and reliable service experience, so we have set up two bug bounty programs according to product categories.
We welcome security researchers/organizations to report security vulnerabilities in our products and services to us. We promise to follow up and respond to your reported security vulnerabilities as soon as possible.
ZTE has been cooperating with GSMA Coordinated Vulnerability Disclosure (CVD) programme to eliminate and mitigate vulnerabilities which are standards-related, for such vulnerabilities you may consider also submitting to GSMA CVD.