Building a Comprehensive Security System for MEC
Security Problems Faced by MEC
Multi-access edge computing (MEC) is one of the core technologies for diverse 5G services. It can flexibly offload traffic through the user plane function (UPF) and push service capabilities and applications to the network edge to improve user experience. Compared with the 4G network, MEC has changed its physical location, service type, and network architecture, and therefore it faces new security challenges:
—Physical security risks: MEC devices are deployed in a relatively insecure physical environment, their management and control capability is weakened, and the network is more vulnerable to threats such as unauthorized access and physical attacks on devices.
—Edge cloud security risks: Operators' network functions and untrusted third party applications are deployed on the edge cloud, which further leads to many security problems such as blurred network boundary, data theft and tampering, and resource isolation. NF/APP version package security and image package can be infected by viruses and Trojans or maliciously tampered.
—User-plane data security risks: The entire core network can be attacked through core network functions that are moved down to the MEC. Data traffic may be illegally intercepted and fraudulently charged.
—MEC platform security risks: Data transmission between the MEC platform and the management system, core network functions or third party applications may be intercepted or tampered. As MEC is deployed close to NR, the air interface communication between the user and NR is vulnerable to attacks like DoS. The MEC platform also has its own security risks such as sensitive data leakage.
—ME APP security risks: Malicious third parties can access the network to provide illegal services. Attackers can access ME APP illegally, resulting in sensitive data leakage. In the ME APP lifecycle management, there are risks of illegal creation, deletion and update.
—MEC orchestration and management risks: The introduction of new management systems and interfaces into the MEC architecture may cause the following security risks: unauthorized access to interfaces such as API, sensitive data leakage, illegal access, and malicious use of management NEs such as the MEC orchestration system.
MEC Security Solution
The MEC environment inherits virtualized network security risks and introduces the security risks related to physical devices, network functions, MEC platform, and APP. Especially in the MEC framework, to achieve interoperability among all layers (CT capabilities and applications, IT applications, MEC platform, hardware, and edge cloud), MEC has to face more security risks.
In response to MEC security risks, ZTE has proposed a hierarchical MEC security framework that covers infrastructure networks, physical facility layer, virtual facility layer, MEC platform, UPF, APP lifecycle, and management security (Fig. 1).
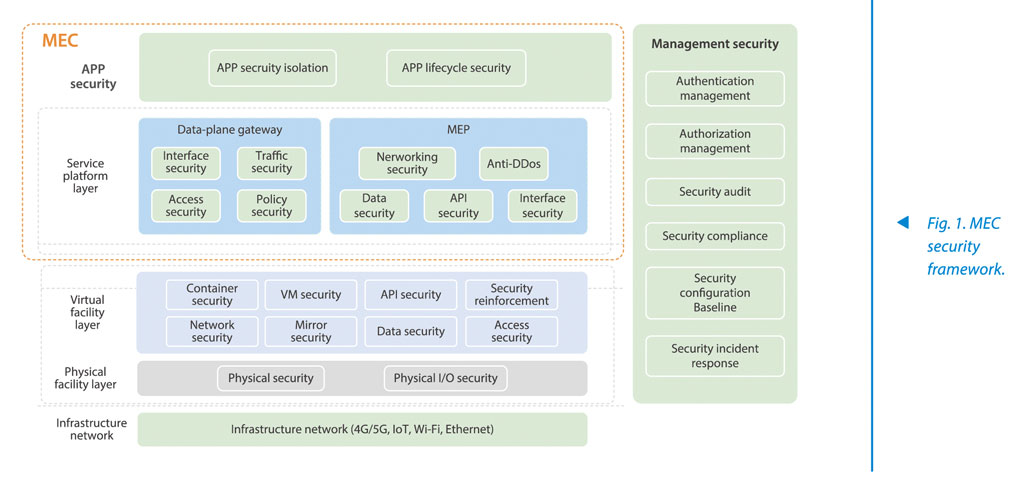
Physical Security
On the physical infrastructure, the security can be ensured through manual means such as locking, monitoring and regular inspection, and access control can be implemented for server input and output.
—Disable local maintenance port of hardware server, such as local serial port, local debugging port, and USB interface,to prevent malicious attackers from accessing and damaging the server.
—Use the IEEE802.1X protocol to authenticate the connected physical network devices to prevent them from being connected to illegal and insecure network devices; encrypt Ethernet frames on the link to prevent L2 interception on insecure physical networks.
Edge Cloud Security
Data with high security requirements needs to be stored in an encrypted mode (such as user ID and access location). For industry high-value data, secure transmission modes including IPsec/TLS are used to prevent data from being leaked or tampered in transmission. Data operations such as data processing, analysis, and usage are authenticated and authorized, and operation logs are recorded.
The security of Host OS, virtualization software and Guest OS is reinforced. Virtual networks are isolated by configuring security groups, access control list (ACL), or deploying virtual firewalls. Trusted computing is used to ensure that the physical server is trusted. The system monitors the operation of virtual resources in real time, detects malicious behaviors, and alerts and isolates them in time.
MEC APP Security
MEC APP is monitored throughout its lifecycle, focusing on user access control, security reinforcement, DoS protection and sensitive data protection. While ensuring that MEC APP is legal, it is also necessary to ensure that users accessing APP are legal.
—Identity security: Integrity protection and authentication are implemented during the registration, loading, and update.
—Mirror security: Security vulnerability and virus scanning are implemented. Mirror files are stored in a secure path and encrypted. Integrity check must be performed for mirror packages during the registration, loading and update.
—Isolation: Strong isolation is implemented between virtual machines (VMs), which involves isolating networks and configuring firewalls, to prevent malicious APPs from attacking other APPs.
—Resource restriction: QoS and SLA management is implemented for APP resources.
—Security termination: All resources are thoroughly purified.
User-Plane Data Security
UPF integrates firewall and security gateway capabilities to ensure the confidentiality and integrity of external data streams, protect confidentiality, integrity and anti-replay for relevant interactive interfaces, encrypt and store configuration data and sensitive information (offload policy) of VNFs to prevent them from being tampered, and implement necessary security reinforcement and physical contact attack protection.
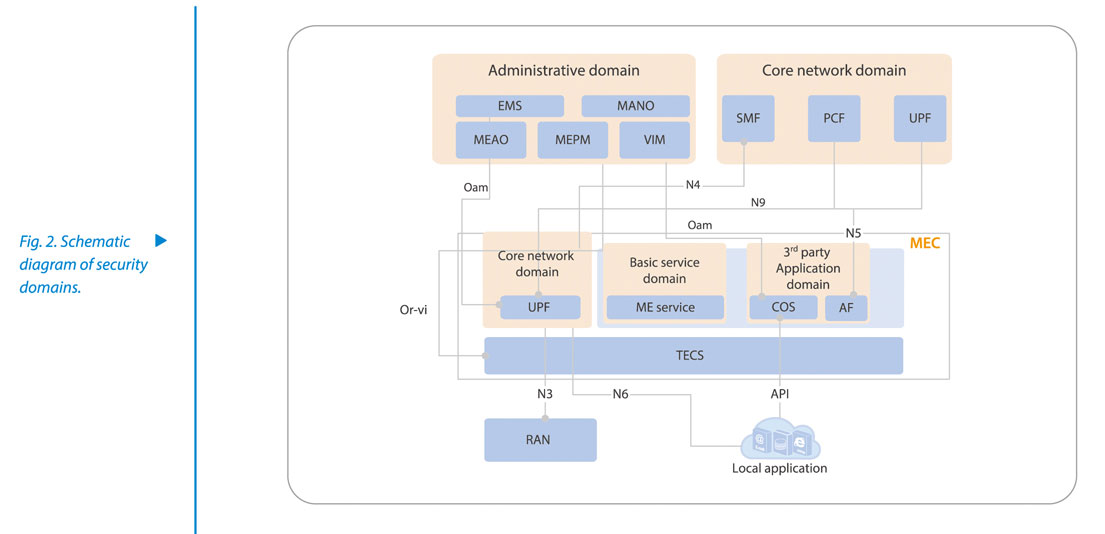
Networking Security
Different security domains are divided according to VNF attributes such as administrative domain, core network domain, basic service domain (location service/CDN), and third party application domain (Fig. 2). Isolation and access control are implemented by dividing different VLAN/VALAN or deploying firewalls.
The system strengthens security protection for user-plane data. Regardless of whether N6 and N9 interfaces are deployed in cities, counties, or lower than those in counties and districts, media-plane bearers need to be isolated and protected through firewalls to protect core network security. For internal signaling services at the N4/N5 interfaces, it is recommended to deploy signaling VPN to carry internal IP private network. IPSEC protection is enabled for services at the N3 interface.Because MEC is connected to multiple external networks, intrusion detection technologies, abnormal traffic analysis, and APT defense system can be deployed as needed to detect malicious software and attacks and prevent threats from spreading further.
Trusted computing technology is used for step-by-step verification from system startup to upper-layer applications to build a trusted MEC platform. To ensure higher availability, a MEC resource pool is established to provide remote disaster recovery and backup capabilities to guarantee service continuity.
Sensitive data of the platform such as user location data and wireless network data should be encrypted and stored, and unauthorized access is prohibited. The API of the platform is authenticated and authorized; the communication with other entities should be authenticated, and the security of the system should be strengthened.
MEC Management and Orchestration Security
The MEC orchestration and management system provides security protection involving system access security, account, API call, ME APP integrity check, and security capability exposure.
—Authenticate, authorize and audit users to ensure that only authorized users can perform operations, and all operations are logged.
—The management system provides unified account management, unified authentication management, and unified network access management.
—The API adopts OAUTH2.0 for authentication and authorization.
—Verify the integrity of software package.
—Consider security capability exposure for MEC applications with a higher security level to meet security requirements.
General Security Management
Following the best security practice in the industry, ZTE uses the vulnerability scanning tool with the latest vulnerability database to regularly scan the MEC system, update the baseline for MEC security reinforcement in a timely manner, and push the configuration baseline for implementation.
ZTE also pays attention to CVE vulnerability announcements and customer security requirements, responds to and handles security incidents, develops and verifies security solutions, and releases them to customers.
As 5G speeds up its commercial launch, MEC will be rapidly promoted and applied as an important service scenario. The security environment of specific MEC application scenarios should be deeply analyzed, and security protection and user data protection should be taken as the necessary conditions for secure MEC operation. ZTE is committed to MEC product security, providing global customers with more secure and trusted 5G products and services.