ZTE's Security Solution Advances Convergence and Innovation of Telecom Cloud Networks
Network function virtualization (NFV) is considered as an advanced and disruptive technological innovation that allows telecom operators to have more open network architecture and more flexible service deployment. NFV decouples hardware and software, that is, by using virtualization technology, general-purpose hardware such as X86 can carry telecom function software, which is more convenient to maintain. This helps telecom operators greatly reduce their Capex and Opex. However, under the NFV architecture, in order to achieve interoperability at all layers, NFV components must be open, which brings open security risks to component interaction. Compared with traditional networks, NFV introduces management and orchestration (MANO) and Hypervisor management software. The introduction of new network elements and the virtualization platform also brings new challenges to security.
Security is a basic requirement of telecom networks. ZTE’s security solution can eliminate the security risks in the NFV system and ensure safe operation of the virtual telecom cloud network.
Architecture of NFV Security Solution
At the beginning of building a telecom cloud network, operators need to examine security threats faced by a NFV system based on the ETSI NFV architecture and build the NFV system without a security blind zone.
Based on the specifications defined by the Cloud Security Alliance (CSA), ZTE has created various components of the telecom network according to the best security practice in the industry and established cloud security checkpoints at various stages during the NFV product lifecycle. ZTE has also developed a series of security initiatives in terms of physical security, NFVI security, VNF security, MANO security, and public security by taking the passing through of the cloud security checkpoints as a necessary condition for this link to be closed. The architecture of ZTE’s NFV security solution is shown in Fig. 1.
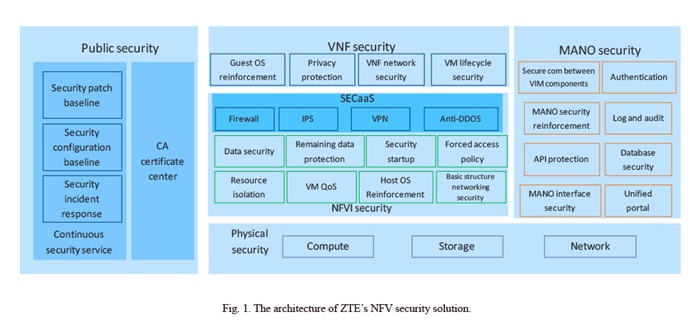
NFVI Security Architecture and Key Technologies
Reliable NFVI security architecture can meet the security enhancement requirements at the NFVI level and provide security as a service (SECaaS) for NFV multi-tenant networks. ZTE’s security solution leverages carrier-grade operation system (OS) as the host OS of NFV and uses multiple key technologies to optimize and reinforce cloud security.
NFVI Networking Security
Secure networking deployment enables isolation between VNF components as well as between infrastructure and VNF services. The infrastructure network is divided into the cloud management network, storage network, service network, and out-of-band management network. The four types of networks must be physically isolated. A network security service chain based on software designed network (SDN) can also be deployed.
Security Startup and Enhanced Hypervisor
ZTE’s security solution provides CPU isolation, memory isolation, network isolation, and storage isolation to ensure resource independence and information security of virtual machines (VMs), and provides Guest/Host instruction space isolation to prohibit a VM running under high privilege mode from threatening another VM. Moreover, a series of QoS guarantees are also applied to VMs. The VM’s CPU, memory, network I/O, and storage I/O resources are set with upper limit, lower limit, and priority control, which can not only carry out common services but also ensure the operation of key services. ZTE’s cloud platform provides an excellent VM resource isolation mechanism and guarantees trusted components of the shared resources through the authentication mechanism.
Data Security
ZTE’s security solution provides the password management function that can manage tenants’ password lifecycle and access control rights. The account password needs to meet the complexity management requirements and is encrypted and saved through message digest algorithms5 (MD5). When transmitting user passwords, ZTE’s telecom cloud network platform uses HTTPS connections to prevent them from being leaked. The solution also provides the storage encryption function that can encrypt VM data before writing it into the disk and ensure user data privacy. The volume in block storage is encrypted when it is mounted on the host, and then the encrypted block device is provided for the VM to use.
VNF Security Solution and Key Technologies
VNF is the functional logic implementation of telecom network elements and also the core information asset of the NFV system. Its security is quite important. ZTE has designed a trusted security solution for VNF that can guarantee security of the entire VNF lifecycle and business process.
Service Networking
Service networking must first consider service network isolation. VNF networks involve VNF-internal and VNF-external interworking. Each interworking network plane of the VNF component (VNFC) has a dedicated virtual network port that connects to the external physical network through the virtual switch (vSwitch) or single-root I/O virtualization (SR-IOV). According to the security risk level, VNF is divided into multiple security domains. Once the interworking traffic between the VNFs crosses the security domain, it must be isolated by the firewall. It is unnecessary to set a firewall for inter-domain interworking traffic between VNFs.
VM Lifecycle
A complete security solution works throughout the lifecycle of VMs and is reflected in all phases of the lifecycle. In the VNF template, NFV needs to use digital signature and MD5 to support integrity verification and source authentication of NSD and VNFD during the registration, loading and update. To meet the security requirements of VNF, the solution designs the affinity and anti-affinity principles and limits the VNFs carrying sensitive data to share the physical server with those VNFs with external access interfaces. The mirror and snapshot of the VM must be stored in a secure path. The storage encryption function is adopted to prevent malicious tampering after illegally authorized access.
MANO Security Reinforcement and Key Technologies
MANO is the control node of NFV. ZTE has developed a security solution to leverage the features of MANO and to prevent global security risks.
Unified Access Portal and Control Node Authentication
ZTE’s security solution implements unified authentication, single sign-on, and log operations of the NFV system. Reverse proxy is used to provide centralized account management and establish global real-name management based on the unique identity. Through centralized access control and fine-grained command-level authorization policies, centralized and orderly operations are managed based on the principle of least privilege. Through centralized security auditing, the system audits the user’s entire operation behavior from login to logout, monitors all sensitive operations of the user to the target device, focuses on key events, and realizes timely and accurate detection of security incidents.
NFVO and VNFM Security Reinforcement
ZTE’s security solution implements multiple security reinforcements for network function virtualization orchestrator (NFVO) and virtual network function manager (VNFM) to ensure VM security, end-to-end security, interface interaction security, and image storage security.
Centralized Log Audit and Secure Resource Recycling
ZTE’s security solution supports centralized log collection and analysis of each node in the NFV system, so that the O&M personnel can know security events and running status of the system in real time. The solution collects and stores operation logs, security logs and system logs generated by the NFV system, and comprehensively records the running status of the system.
The NFV-based telecom cloud network is more complex, flexible and open than a traditional telecom network. While providing a technical basis for the IT telecom network, the NFV system also brings more security risks and poses potential hazards and challenges to NFV commercial networks. Telecom operators need to comprehensively review potential security threats in the NFV systen based on the ETSI NFV architecture and to form a multidimensional, in-depth security protection solution to block security vulnerabilities. Moreover, in daily operation and maintenance, operators need to establish a professional network security service team. They can set up a sustainable telecom network security service guarantee system to protect the security of telecom cloud networks.