Intelligent Configuration Check Based on Role Fingerprint
With the rapid development of emerging services and the continuous expansion of network scale in the 5G era, the network architecture presents multi-dimensional complexity. Operators will face a large amount of new network construction and old network transformation, resulting in huge work of infrastructure configuration. Due to the complexity of 5G network route management and the increasing difficulty in multi-layer logical network operation, there will be an exponential growth in network O&M. It is therefore urgent to introduce AI technologies and algorithms such as big data and machine learning to improve the automation of network O&M and address its difficult issues.
ZTE and the Guangdong branch of China Unicom (Guangdong Unicom) have jointly launched the role fingerprint-based intelligent configuration check. This function uses AI technologies and algorithms for big data analysis to quickly discover abnormal network configurations and potential risks.
Functional Mechanism
Each network has different size, topology and service combination. There are differences in the configuration of each network element (NE) and each service, which makes the configuration work huge and easy to make mistakes. However, the internal network substructures such as NE roles and service types are very similar. If the general substructure model inside the network can be extracted and used for abnormal experience analysis, the operating cost can be greatly reduced. This solution uses the knowledge graph technology to extract the configuration features of devices from the existing network to form role fingerprints, identify abnormal configurations, and provide guidance for deployment and maintenance of new networks.
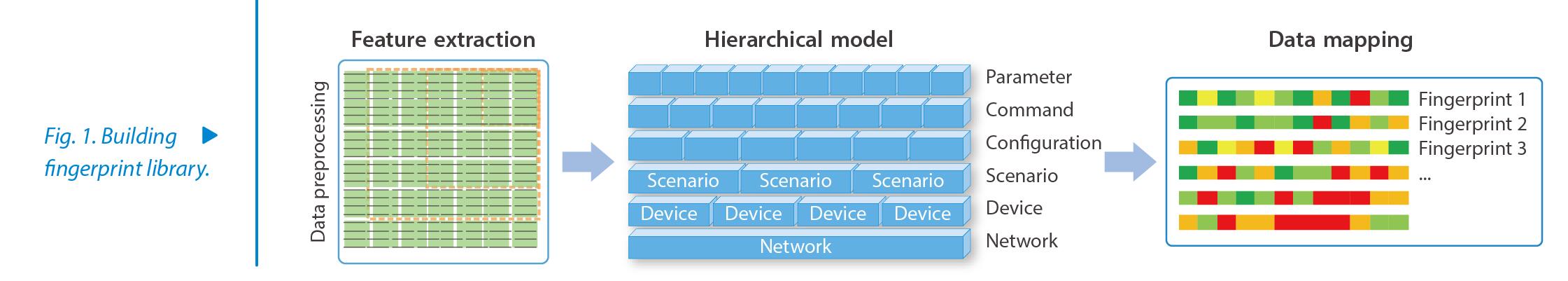
What's Role Fingerprint
Role fingerprint is actually synonymous with data features, which was first put forward by ZTE and Guangdong Unicom. For example, a person’s voice has certain voiceprint features. We use machine learning to extract the frequency, waveform and other features from the voiceprint to build a model. This data model is called the role fingerprint. With the role fingerprint, the next time the person speaks, the system can identify the person. Similarly, you can build a role fingerprint for a device based on data characteristics of the device configuration.
How Does Configuration Check Work
The configuration parameters of a device are determined by its type, services it carries, topology and connectivity features in the network. Role fingerprint represents particular features of a set of configuration parameters for a particular type of device.
Which Abnormal Configuration Can Be Checked
The configuration check function is integrated in the intelligent transport control and management system ZENIC ONE. It supports all ZTE IPRAN equipment types in the existing SDN network. The abnormal types that can be checked include parameters, sub-commands, and command combinations. At present, the faults that can be checked are mainly caused by incorrect configuration, missing configuration, and configuration conflict. Incorrect and missing configurations can be pre-checked through the role configuration knowledge graph. Configuration conflict can be avoided by actively checking network architecture through the reasoning knowledge graph generated from the inspection rules.
Application
The traditional way of configuration check depends on the manual operation of engineers. They find problems according to their expert experience. ZTE and Guangdong Unicom have innovatively applied AI technologies including the knowledge graph to the transport network and have proposed a new concept of role fingerprint for intelligent configuration check. At the MWC Shanghai in June 2019, ZTE and Guangdong Unicom jointly demonstrated the role fingerprint-based intelligent configuration check for the first time. This application won the Best Network Intelligence Award at the Broadband World Forum (BBWF) held in Amsterdam, Netherlands in October 2019.
According to Guangdong Unicom O&M team who tested the role fingerprint-based intelligent configuration check on their IPRAN data from typical cities in Guangdong province such as Shenzhen, Foshan, and Dongguan, it took only one person in less than 10 minutes to check the configurations of nearly 1000 devices in the IPRAN networks, and the accuracy of abnormality check rate reached 85%.
The application is also tested and verified in the 5G network of Shenzhen Unicom. It helps Guangdong Unicom check 5 million configurations for 5000 devices in a new 5G network. Compared with the traditional check solution that needs several O&M personnel to work for several days to deal with the data in one city, the role fingerprint-based intelligent configuration check solution drastically reduces labor cost and significantly improves network O&M efficiency.
The role fingerprint-based intelligent configuration check solution has been deployed by operators in their existing networks. It improves the efficiency of configuration check and the identification rate of configuration risk, which ensure the quality of network operation. Also, it significantly saves manpower in O&M through machine computing, thus reducing Opex and meeting operators' needs for low-cost, high-speed, and highly reliable 5G networks.